Voting Process

Before starting a vote, the Voting Administrator prepares to launch a new vote by purchasing Punk Tokens to be distributed as rewards to voters from the Punkpoll liquidity pool.
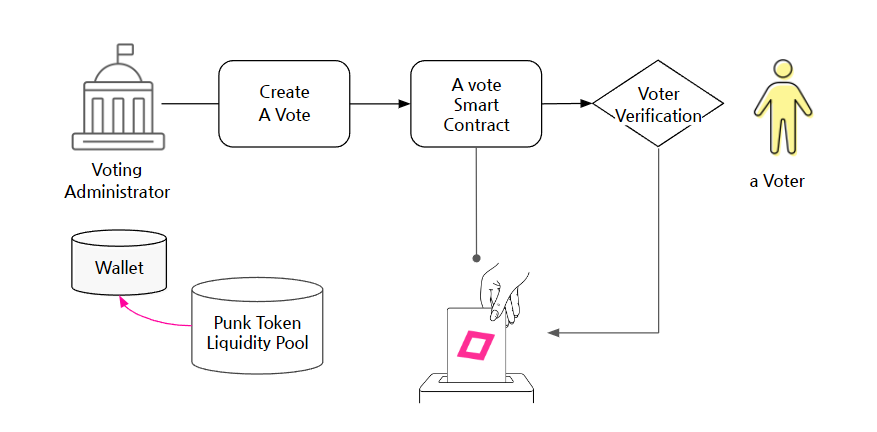
- Creating a Vote: The Voting Administrator sets up a new vote in the vote builder (voting content, voting conditions, voter registration, rewards in Punk Tokens for voters, etc.).
- Voting Smart Contract: The created vote is managed by a voting smart contract on the blockchain, which automatically executes the rules and conditions of the vote.
- Voter Verification: Voters are verified and authenticated by the voting authority (election commission), and a specific vote token (zk-Vote-nft) is issued for that particular vote.
- Voting Fee: The usage fee for the Punkpoll voting service is set as a certain percentage of the Punk rewards paid to each voter, determined through the voting smart contract. If election-related information needs to be sent to voters via text message in advance, the cost is calculated and set in the same manner.
Voter Authentication Method
Although the Punkpoll decentralized voting system operates all processes, the voter verification, authentication, and token issuance after authentication are mostly handled by the voting authority. In this case, the following process is followed based on the Punkpoll voting smart contract.
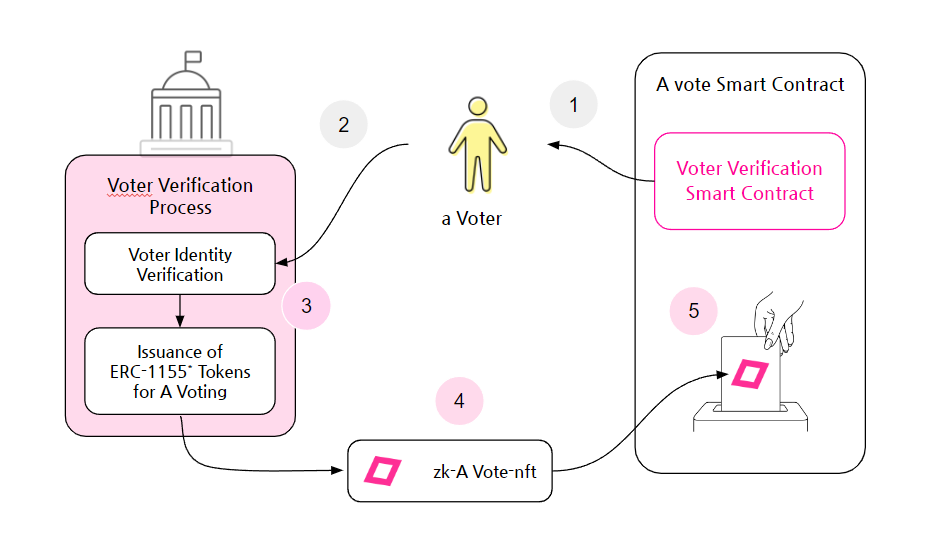
The process for a voter authentication smart contract (if ERC-1155 is used) is as follows:
① Notification: The voter verification smart contract from 'A Voting Smart Contract' sends a voter verification notification to the voter.
② Verification Request: The voter requests voter verification from 'A Election Commission'.
③ Authentication: 'A Voting Election Commission' verifies the voter's real identity.
④ Token Issuance: 'zk-A vote-nft (token)' is issued.
⑤ Voting: The voter votes using the 'zk-A vote-nft (token)' issued by the 'A Election Commission'.
ERC-1155 is a token standard based on the Ethereum blockchain, designed to handle multiple types of tokens under a single contract. In voting, it is efficient for issuing and managing voters' ballots as NFTs and facilitates batch transfers.
Voting Smart Contract Process
Punkpoll's voting smart contract, based on a zero-knowledge blockchain, provides a trustless environment that protects the privacy of voters. It offers an automated process for voter authentication, zk-vote issuance, receipt processing, reward distribution, and result announcement, according to the voting conditions.
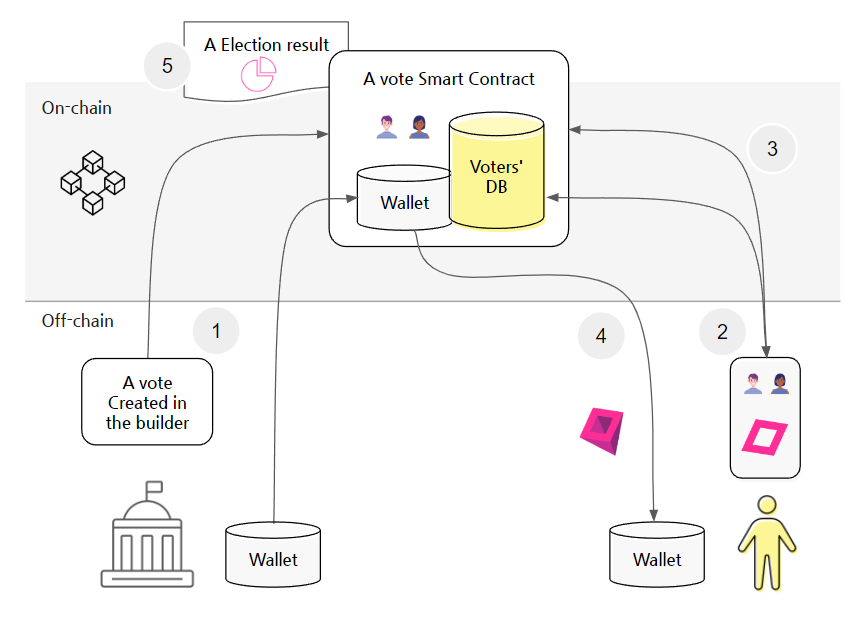
① The Voting Administrator creates 'A Vote (voting smart contract)' in the Punkpol builder and registers it on the blockchain (on-chain).
Once the smart contract is registered on the blockchain, it operates automatically based on the conditions without the organizer's involvement.
② Participants notify voters through text (messenger messages, etc.), and if their identity is verified as a voter with zk-PUNK, 'zk-A vote-nft' is issued to them.
③ Voters cast their votes using 'zk-A vote-nft.'
④After voting, 'zk-A vote-receipt-nft' and reward PUNK Tokens are sent to the voter's wallet.
⑤ Once the vote concludes, the results for 'A Vote' are announced.
The roles of off-chain and on-chain in the blockchain:
Off-chain role: In the voting builder, 'specific votes' and voter information etc., to be recorded on the blockchain (tx) are created, and zero-knowledge proofs for these contents are generated. In this process, Mina Protocol verifies these transactions off-chain before uploading them to the blockchain.
On-chain role: 'Specific votes' are registered on the blockchain (on-chain) as a smart contract structure, where the security and transparency of the blockchain are enhanced using zk-SNARKs technology.
Verifying My Vote Through the Voting Receipt
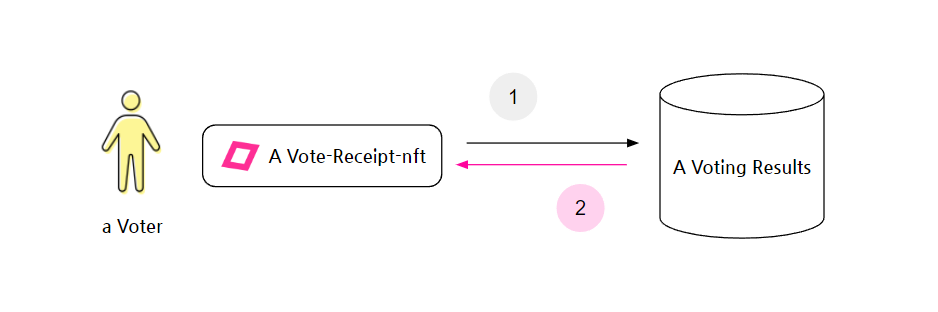
After voting, voters can use the ① receipt (zk-A vote-receipt-nft) they received to ② check if their vote was correctly included in the voting results. Although the voting receipt and results are based on zero-knowledge proofs, which means the contents of the vote can't be verified, voters can still confirm whether their vote was included in the results.
In voting, coercion resistance is important. Coercion resistance refers to the protection of an individual's choices or will from external pressure or coercion. This is particularly crucial in voting systems, ensuring that voters do not have to disclose their choices to specific parties and are protected from any negative consequences resulting from their decision.
Voting Result Analysis
The analysis of voting results is conducted using the zk-PUNK (NFT) of participating voters. This method of analyzing vote outcomes assists in acquiring significant statistical data while vigorously safeguarding individual privacy. The usage of zk-PUNK (NFT) in this context is pivotal for maintaining the integrity of the process. However, careful management is crucial during the analysis to prevent compromising voter anonymity, particularly in situations with a limited number of participants or where there is a risk of excessive data segmentation.
The zk-PUNK(nft) voting system analyzes the validity and reliability of voting results using statistical analysis methods such as statistical threshold and k-anonymity. The statistical threshold provides a criterion for determining whether the voting result is statistically valid, and k-anonymity is a method for protecting personal information where voter information is displayed tied to a minimum of k voters.
By utilizing these statistical methods, we can statistically analyze the validity of the vote, increase the accuracy of the results, and protect voters' personal information. This method is essential in maintaining the transparency and accuracy of voting in the blockchain-based voting system while respecting the importance of privacy protection.
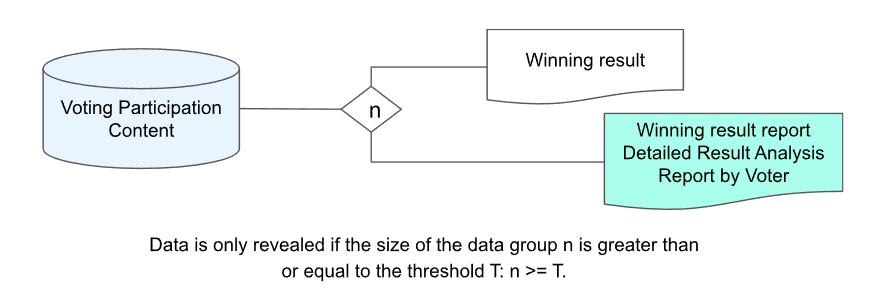
The statistical threshold opens the voting results of the group only when the number of voters in a specific group exceeds the threshold (for example, 10). This method only discloses specific information like '1 vote by a man in his 20s', '1 vote by a woman in her 30s' only in groups where there are more than 10 voters, thereby preventing the exposure of voting preferences of a minority of voters.
Meanwhile, k-anonymity is a method in which each voter's information matches at least k-1 other voter's information. This method prevents the exposure of an individual voter's voting preference by generalizing or grouping the voter's information such as age, gender, and region. For example, if k is set to 5, each voter's information will match with at least 4 other voters' information.
These two methods are applied depending on the situation and objectives. When there are few voting participants, it is appropriate to use a statistical threshold to disclose voting results, and when there are enough respondents, it is appropriate to use k-anonymity to protect individual voter preferences.
In addition, it provides a method to protect personal information while analyzing the reliability and accuracy of voting results using statistical methods like the statistical threshold and k-anonymity. Through this, it can increase the reliability of the voting results and balance privacy protection and transparency.
Statistical Thresholds: This is a method of not disclosing data from minor groups. This is primarily implemented as a method of disclosing data only when the size of the group is greater than or equal to a certain threshold. Data from a group of size n is only disclosed if n is greater than or equal to the threshold T: n >= T.
k-anonymity: This is a method of making each individual data point appear identical to at least k-1 other data points. This is typically implemented by generalizing or grouping some attributes of the data. Mathematically, each data point is guaranteed to have at least k identical tuples in the dataset.
#zkVoting #zkVote #zkVotingSystem