Social Graph Authentication
All users of Punkpoll are composed of authenticated members*1. By completing the registration and verification process, users around the world attain the status of 'Punkpoll citizens' and are granted 'zk-PUNK (nft)' to participate in voting and surveys. This 'zk-PUNK', based on zero-knowledge proof, plays a crucial role in services requiring real-name verification while ensuring user privacy.
Punkpoll employs two main methods of authentication:
Firstly, in the messenger-based voting and survey services, the 'Social Graph Authentication' method is used, where users authenticate each other's identities.
Secondly, in voting services, real-name verification is carried out through an organizer's voter verification process.
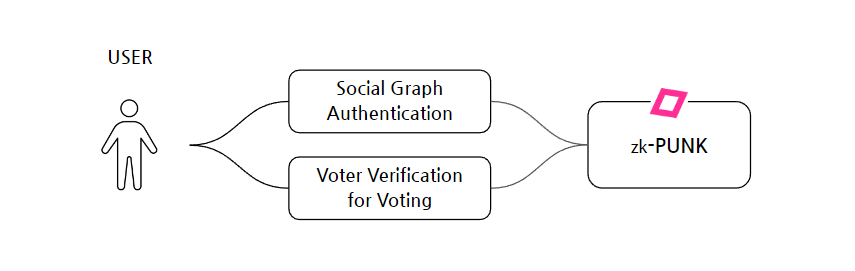
*1 Punkpoll's method of authentication is primarily based on the Social Graph Authentication method, and for voting, the authentication is conducted according to the methods set by the organizer, which fundamentally includes KYC and nationally recognized certification for voter verification.
Social Graph Authentication
Punkpoll uses 'Social Graph Authentication' for registration and verification. This method utilizes everyday messenger applications, allowing users to verify each other's real existence based on the 'Web of Trust' mechanism. Unlike traditional document-based authentication methods, this approach enables identity verification based on actual human relationships and is a key part of the decentralized Punkpoll registration process.
Users join Punkpoll using their most commonly used messenger account. After joining, they initiate the verification process by sending a message to their friends asking for authentication. When a friend authenticates a user, mutual authentication occurs, where that friend is also authenticated by the user. This method is established through existing friendships, forming a trustworthy network.
Furthermore, Punkpoll is developing a feature in the Punkpoll Wallet that allows users to retrieve their private keys through authentication from at least three people. This method, which establishes trust and identity verification through interconnected relationships, does not rely on centralized authentication authorities but uses trust relationships formed in real life as the basis for digital identity verification. By mutually authenticating each other's identities, users create a reliable network within the Punkpoll platform, serving as strong social proof for identity verification. This approach aligns with Punkpoll's principle of decentralization and plays a crucial role in verifying the authenticity of individuals in online interactions.
Social Graph Authentication Mechanism
Registrants join Punkpoll using the 'Messenger' they most commonly use in their daily life. It is advisable to register using a messenger utilized more with family and friends than for work purposes, as this will facilitate easier authentication of one’s existence.
The authentication process is as follows:
- Sharing Authentication Request: After registering, users request their family or friends to join Punkpoll and authenticate their existence.
- Mutual Authentication Mechanism: Family or friends authenticate the user, and simultaneously, they also receive mutual authentication. This process requires at least three family members or friends.
- Authentication Circulation: Those who have authenticated the user can also receive authentication from other people. This method strengthens the reliability of the entire network.
- Building Trust on the Platform: The trust graph formed through mutual authentication contributes to enhancing the overall trustworthiness of the platform.
- Spread of Authentication Effect: Once a user is authenticated by trustworthy individuals, their reliability within the platform is reinforced, enabling them to participate in various activities (such as voting and surveys).
- Privacy Protection: The authentication process, conducted using familiar tools like messengers, maintains personal privacy and promotes a decentralized approach.
- User Convenience: By using everyday and familiar tools like messengers, users can complete authentication in a simple and practical manner without complicated procedures..
This method is based on natural connections and trust among users, consequently building a strong foundation of trust for the platform and enabling users to efficiently prove their existence.
Social Graph Authentication and Reward Structure
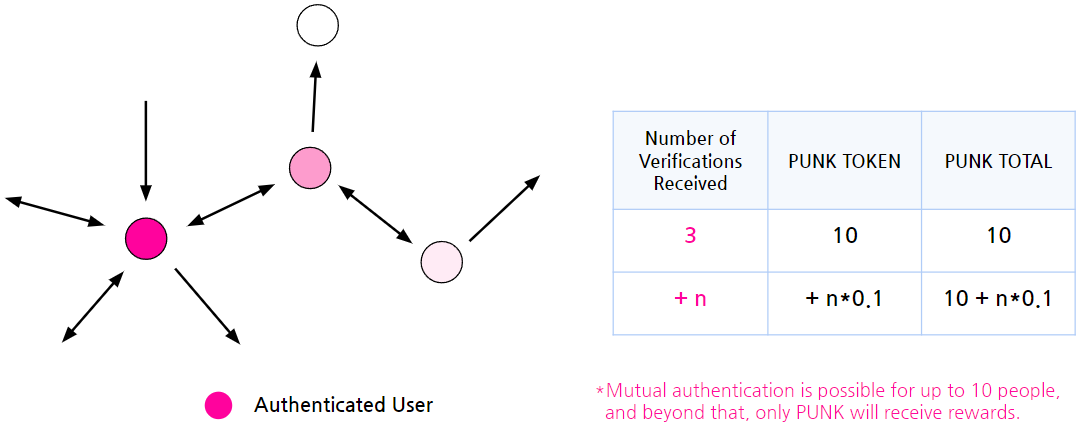
The 'Social Graph Authentication' system incorporates the following reward mechanism: Update 2024.2.5
- PUNK TOKEN Mining Rewards: Upon joining PunkPoll, 100 PUNKs are mined, and users receive 10 PUNK TOKENS as a mining reward. However, these tokens (100 PUNK) remain in a 'Lock-up' state and cannot be used until the user receives verification from at least three people.
- Rewards Unlocking After Authentication: Once a user receives authentication from more than 3 people, the Lock-up on the previously awarded 10 PUNK TOKENS is released. From this point, the user can utilize the tokens. *As of February 5, 2024, the average mutual authentication is 11.18 people.
- Additional Rewards for Additional Authentication: After mutual authentication with more than 3 people, for every additional person, 0.1 PUNK is awarded as a reward. *Refer to the table above
- Limit of Rewards: Mutual authentication is only possible up to 10 people per individual, and beyond that, rewards are given in PUNK TOKENS only.
This reward structure encourages users to actively interact and build trust within the PunkPool network, while also promoting the platform's activation.
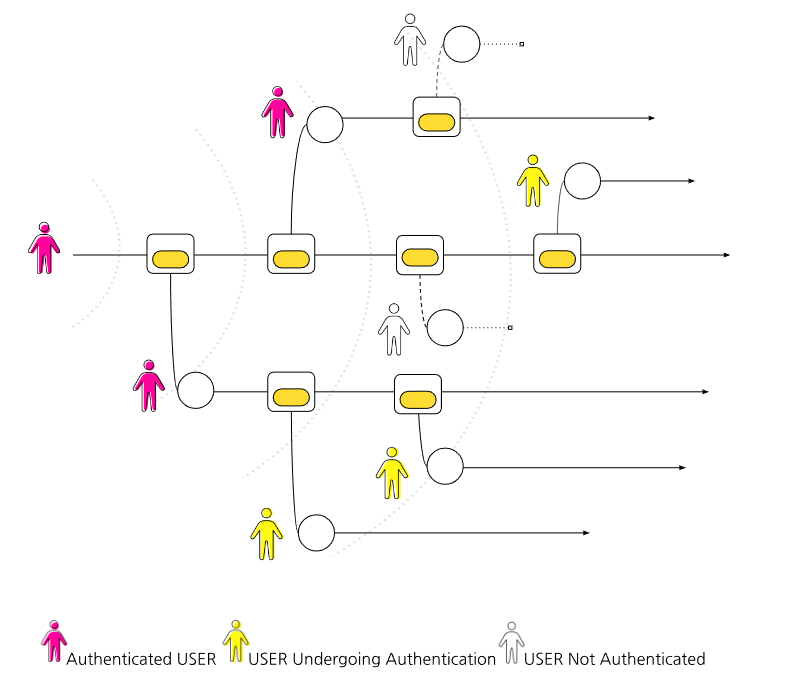
Social Graph Authentication Process (Messenger)
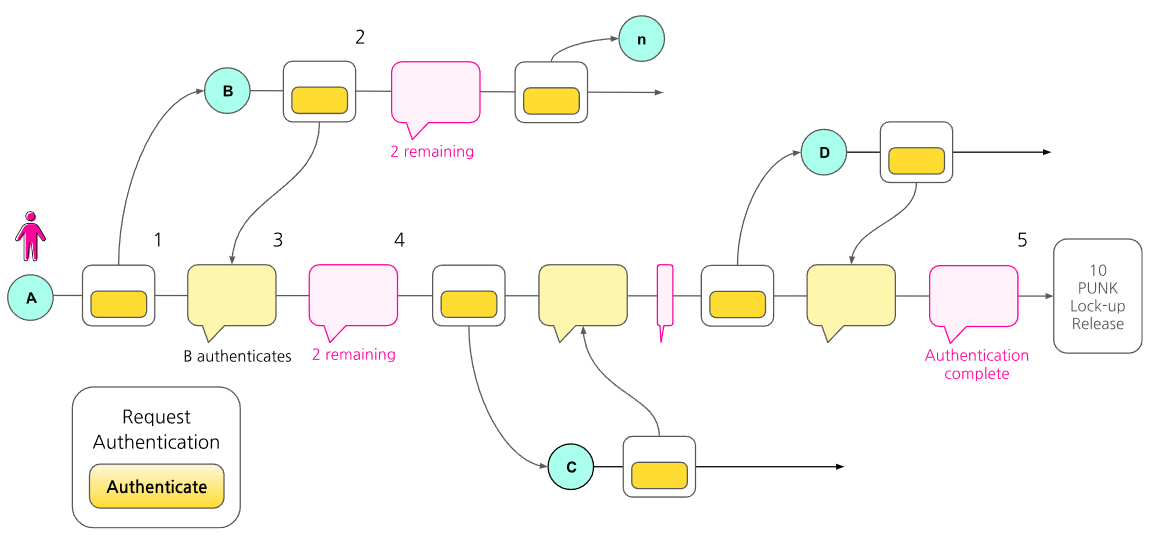
Punkpoll Social Graph Authentication Procedure:
- User A joins the Punkpoll platform through their regularly used messenger application. (Upon registration, 10 PUNK TOKENS are allocated, which are locked up until the authentication is complete.) Subsequently, A sends a message through the Punkpoll channel in the messenger to their friend B, requesting them to authenticate A.
- Friend B checks the authentication request message from A and joins Punkpoll through the same messenger's Punkpoll channel. B then agrees to A's authentication request and completes the authentication process.
- The Punkpoll system sends a notification to A that 'B has completed the authentication' and informs them that A and B are mutually authenticated.
- Punkpoll notifies A that two more authentications are required to complete the process. (This process is repeated until three authentications are completed.)
- Once A completes authentication from a total of three people, Punkpoll sends a notification of completion. (It informs that the lock-up on the 10 PUNK TOKENS allocated at registration is released and they are now available for use.)
After the initial user invites and authenticates three friends, they become mutually authenticated. Subsequently, friends who have been invited and authenticated only need to receive authentication from two friends.
*Reference: Tom's Social Graph Authentication Process
Tom authenticates himself through his friends as follows:
- Tom joins 'Punkpoll' with his Messenger ID.
- Tom accesses his friend list on 'Messenger'.
- Tom sends a message to his friend Dick on 'Messenger' asking him to authenticate him.
- Dick joins 'Punkpoll' and authenticates that Tom is his friend (mutual authentication).
- Similarly, Tom sends messages to Harry and Bob asking them to authenticate him.
- Harry and Bob join 'Punkpoll' and authenticate that Tom is their friend (mutual authentication).
- Tom gets authenticated by three friends.
- "Punkpoll"notifies Tom that he has been authenticated through his friends.
This way, Tom gets his existence authenticated by close friends (from 3 up to 10 people).
*Subscriber Diffusion Speed and Prediction
By creating a prediction model, we can see that:
- Initial Conditions:
- Initial number of subscribers I0 (e.g., 1,000 people)
- Number of friends invited by the initial subscribers for authentication G1 (e.g., 3 people)
- Number of friends invited by each authenticated user later G2 (e.g., 2 people)
- Time taken for an invitation Tinvite (e.g., 2 days)
- Time taken for authentication Tverify (e.g., 2 days)
- Invitation rate weight W (e.g., ⅔, i.e., 66%)
- Daily User Increase Formula:
- The number of new users invited on day n, Nn, is the number of users who were invited and authenticated before day n multiplied by the growth rate and invitation rate weight:
Nn = Nn - Ninvite- Nverify x G x W
- Cumulative Number of Users Calculation (with a weight of 66%):
- The total number of users accumulated on day n is the sum of the accumulated number of users up to the previous day plus the number of new users invited on day n
Cn = Cn-1 + Nn
Simulation:
- With an initial number of subscribers of 1000, and an invitation weight of 66%, in 100 days => 3,226,844 people
- With an initial number of subscribers of 1000, and an invitation weight of 50%, in 100 days => 25,000 people.